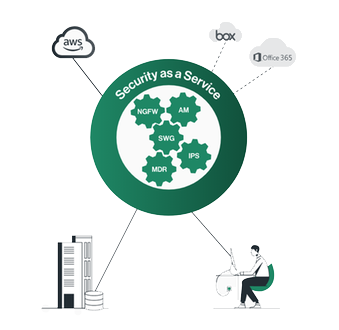
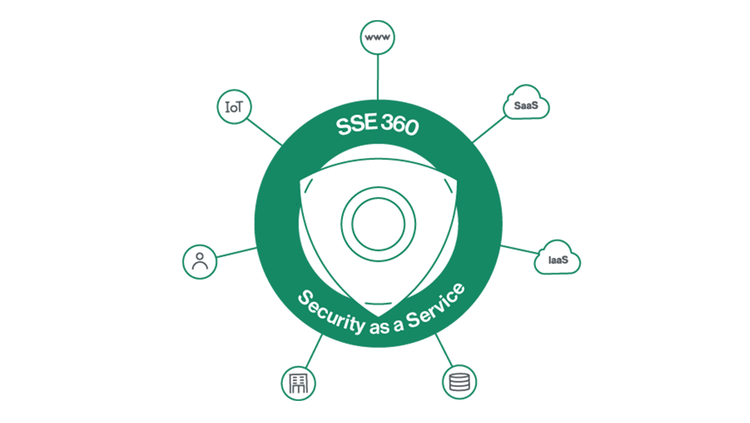
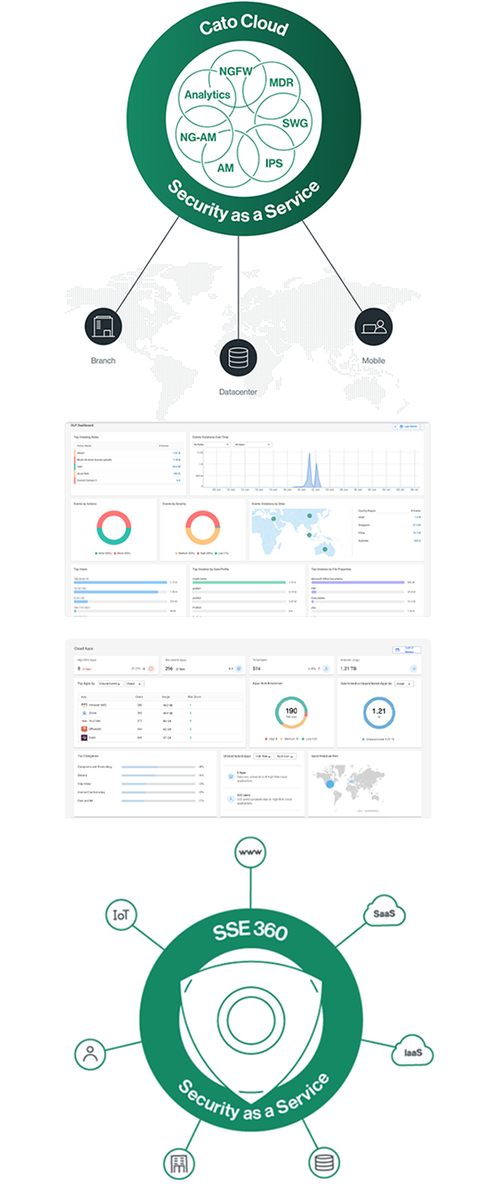
Security services cover access control and threat prevention
Cato, the cloud-native carrier, provides the only secure managed SD-WAN service built with a global reach, self-service, and agility of the cloud. We replace security point solutions with a converged, uniform security stack built for the digital business. Our security as a service is a set of tools built directly into our cloud network as part of a tightly integrated software stack. Because of this, it can be applied consistently across all traffic traversing the network, eliminating the need for disparate edge security devices. Security services cover access control and threat prevention and are powered by our security research labs.
Top Features
Security as a service for today’s enterprises
No more capacity planning, software upgrades, operational complexities, or hidden costs. Maintain granular control of all your security policies with easy configuration through Cato’s centralized management portal. All PoPs are interconnected using fully-meshed, encrypted tunnels. Customers connect to Cato through encrypted tunnels, established by Cato Socket or through IPsec tunnels from existing security appliances.
Managed threat detection and response to reduce dwell time
Cato’s Managed Threat Detection and Response Service (MDR) enables enterprises to offload the resource-intensive and skill-dependent process of detecting compromised endpoints to the Cato SOC team. Cato seamlessly applies a full MDR service to customer networks. They automatically collect and analyze all network flows, verify suspicious activity, and notify customers of compromised endpoints.
Advanced threat prevention
As part of Cato’s Advanced Threat Protection, Cato offers anti-malware protection and Intrusion Prevention System (IPS) capabilities. Both services inspect WAN and Internet traffic. Additionally, Cato PoPs inspect TLS-encrypted traffic in the Cato Cloud, so there are no scaling constraints or additional latency.
Access control across your network
Get access control capabilities through the next-generation firewall (NGFW) and secure web gateway (SWG). NGFW provides full application awareness with the ability to inspect the payload of packet data and distinguish between different types of web traffic. Cato’s SWG allows customers to monitor, control and block access to websites based on predefined and customizable categories.
Recommended products
Security as a Service for Today’s Enterprises
With Cato’s security as a service, you gain the benefit of consistent security across your entire network while offloading the day-to-day management to Cato. No more capacity planning, software upgrades, operational complexities, or hidden costs. At the same time, you maintain granular control of all your security policies, with easy configuration through Cato’s centralized management portal. The network was designed with security in mind. All PoPs are interconnected using fully-meshed, encrypted tunnels. Customers connect to Cato through encrypted tunnels, established by Cato Socket (a zero-touch appliance deployed at physical locations), or through IPsec tunnels from existing security appliances.
Access Control Across your Network
Cato provides enterprises with access control capabilities through the next-generation firewall (NGFW) and secure web gateway (SWG). NGFW provides full application awareness with the ability to inspect the payload of packet data and distinguish between different types of web traffic. Cato’s SWG allows customers to monitor, control and block access to websites based on predefined and customizable categories.
Next-Generation Firewall
The Cato NGFW inspects both WAN and Internet traffic. It can enforce granular rules based on network entities, time restrictions, and type of traffic. The Deep Packet Inspection (DPI) engine classifies the relevant context, such as application or services, as early as the first packet and without having to decrypt the payload. Cato provides a full list of signatures and parsers to identify common applications. In addition, custom application definitions identify account-specific applications by port, IP address, or domain.
Secure Web Gateway
Cato provides an SWG to give you granular control over your Internet-bound traffic, enabling enforcement of corporate policies and preventing downloads of unwanted or malicious software. They provide predefined policies for dozens of different URL categories and support custom rules, enhancing the granularity of web access control. As with the rest of the service, the SWG is easily managed through Cato’s management portal and covered by a full audit trail.
Advanced Threat Prevention
As part of Cato’s Advanced Threat Protection, Cato offers anti-malware protection and Intrusion Prevention System (IPS) capabilities. Both services inspect WAN and Internet traffic. Additionally, Cato PoPs inspect TLS-encrypted traffic in the Cato Cloud, so there are no scaling constraints or additional latency.
Anti-Malware
Malware Detection and Prevention leverages multi-layered and tightly integrated anti-malware engines. First, a signature and heuristics-based inspection engine, which is kept up-to-date at all times based on global threat intelligence databases, scan files in transit to ensure effective protection against known malware.
IPS Protection Engine
Cato delivers a fully managed and adaptive cloud-based IPS service. Cato Research Labs updates, tunes, and maintains context-aware heuristics, both those developed in-house (based on big-data collection and analysis of customers’ traffic) and those originating from external security feeds. This dramatically reduces the risk of false positives compared to other IPSs that lack an experienced SOC behind them. Cato Cloud scales to support the compute requirements of the IPS rules, so customers don’t have to balance protection and performance to avoid unplanned upgrades as processing load exceeds available capacity.
Managed Threat Detection and Response to Reduce Dwell Time
Cato’s Managed Threat Detection and Response Service (MDR) enables enterprises to offload the resource-intensive and skill-dependent process of detecting compromised endpoints to the Cato SOC team. Cato seamlessly applies a full MDR service to customer networks. They automatically collect and analyze all network flows, verify suspicious activity, and notify customers of compromised endpoints. This is the power of networking and security convergence to simplify network protection for enterprises of all sizes.
Additional Information
Terms & Conditions
Terms of Service
https://www.catonetworks.com/msa/Privacy Policy
https://www.catonetworks.com/privacypolicy/Support
Knowledge Base
https://www.catonetworks.com/Read Documentation
https://www.catonetworks.com/cato-sase-cloud/enterprise-grade-security-as-a-service-built-directly-into-the-network/Resources
Cato Networks Security as a Service - Overview
Powered by WHMCompleteSolution