Protects against highly sophisticated threats
1.80/month
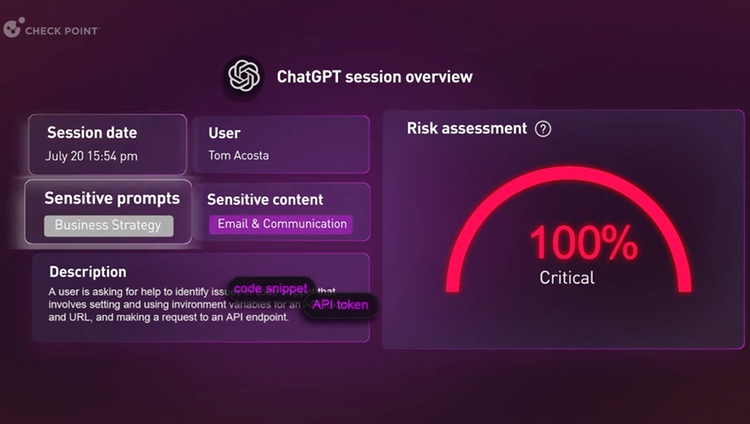
Check Point Harmony Endpoint is an advanced cybersecurity solution designed to protect endpoint devices, including desktops, laptops, and mobile devices, from a wide range of cyber threats. It integrates multiple security technologies into a unified platform to provide comprehensive protection against malware, ransomware, phishing, and other sophisticated attack. It includes advanced endpoint detection and response (EDR) capabilities. These features enable security teams to investigate and respond to security incidents swiftly and effectively. EDR functionality provides detailed visibility into endpoint activities, allowing for the detection of suspicious behavior and the remediation of potential security incidents.
Top Features
Single agent
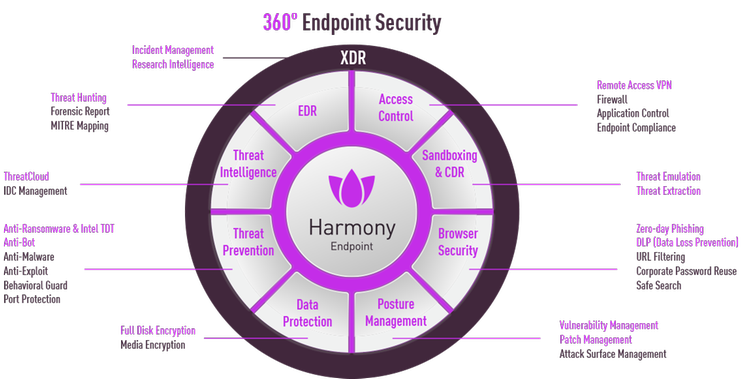
EPP, EDR & XDR, all in a single client and management console.
Flexible management
With an easy deployment for on-prem, cloud, or MSSP management.
Extensive OS support
With a wide range of supported operating systems, including Windows, Mac, Linux, Servers, VDI, browsers, and mobile devices.
Threat intelligence
Check Point’s Threat Cloud Al provides zero-day protection with more than 60 AI engines.
Recommended products
Harmony Endpoint protects against the most imminent threats:
Cyberattacks are constantly increasing in volume and sophistication with a 38% rise in the number of cyberattacks year-over-year.
Ransomware & malware protection
Fortifying organizational data against sophisticated ransomware attacks.
Posture management
Reduce the attack surface with automated vulnerability & patch management.
Zero-phishing & browser protection
Blocks the most sophisticated phishing attacks with zero impact on end users.
Data protection
Safeguarding Sensitive Data Loss with advance DLP. Capabilities and unique Full Disc Encryption, to keep valuable data safe and maintain compliance and regulation.

Additional Information
Resources
Check Point Harmony Endpoint - Introduction
Harmony Endpoint is a complete solution that protects the remote workforce from today’s complex threat landscape. It prevents the most imminent threats to the endpoint, such as ransomware, phishing, or drive-by malware.
Check Point Harmony Endpoint - Datasheet
Mobile and Endpoint Bundle Complete
CP-HAR-MOBILE-DVC-EP-COMPLETE-BUN $7.22 Device/Month$85.00 Device/Year
Mobile and Endpoint Bundle Advanced
CP-HAR-MOBILE-DVC-EP-ADVANCED-BUN $5.35 Device/Month$63.00 Device/Year
Security Awareness Training
CP-HAR-EC-PHISH-AWARENESS-T$18.00 User / Year
User/Year
$2.00 User / Month
User/Month
Powered by WHMCompleteSolution