Monitoring PII, PCI, PHI & NPI under regulations like FISMA & SOC2
$4.00 /month
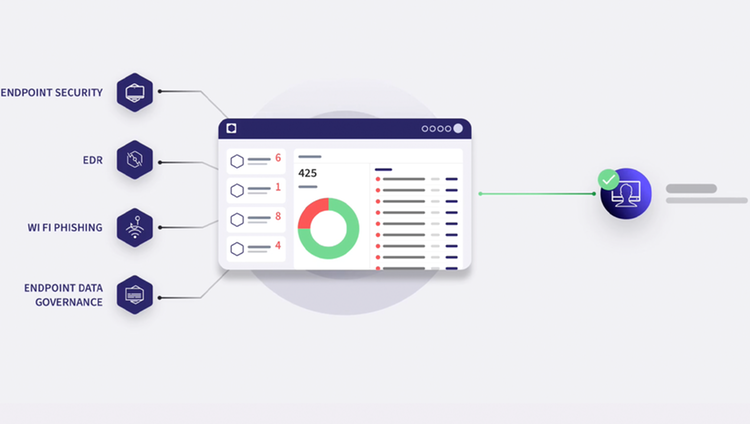
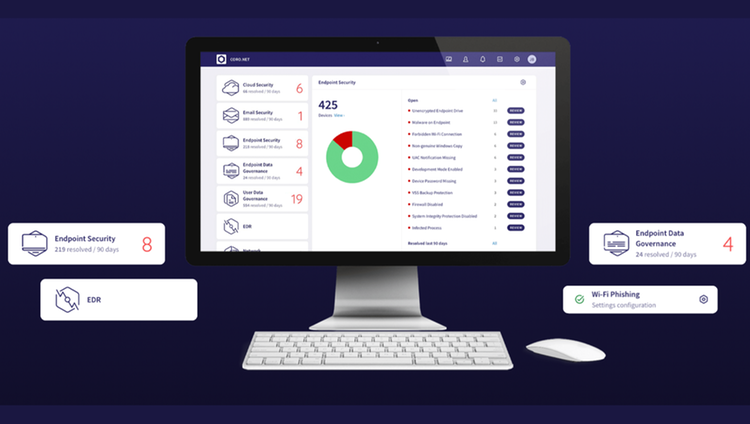
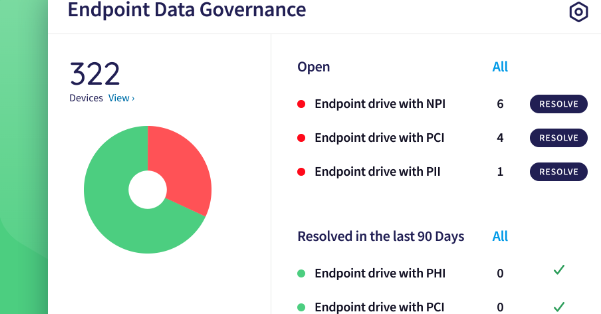
Coro Endpoint Data Governance Module helps administrators establish a strategy for correctly and securely handling sensitive data by authorized users on their endpoint devices. We protect sensitive data from unauthorized access, use, disclosure, modification, or destruction across endpoints. The module enables remote scans on connected endpoint devices to analyze device storage for sensitive data assets and raise tickets for positive results. We also provide strong data governance monitoring to aid compliance with regulatory standards and alerting where exposure of controlled data appears to violate regulations.
Top Features
PII (Personally identifiable information)
PCI (Payment card information)
PHI (Protected health information)
NPI (Non-public information)
Recommended products
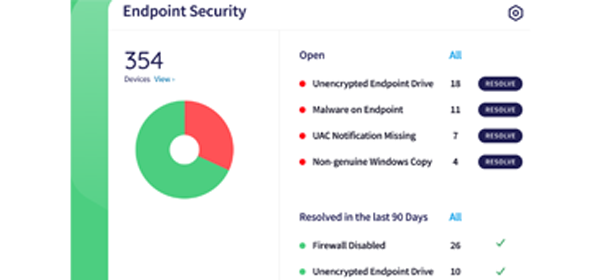
Endpoint Security
Endpoint Security is the core endpoint module in Coro.
Capabilities:
- Next-gen Antivirus: Advanced threat protection (ATP) analyzes both static files and running processes for anomalies.
- Allow/Block Lists: Create lists of files, folders, and processes to allow or block on your protected endpoints.
- Device Posture: Apply policies to users or groups and determine the remediation action for vulnerabilities.
Endpoint Detection and Response
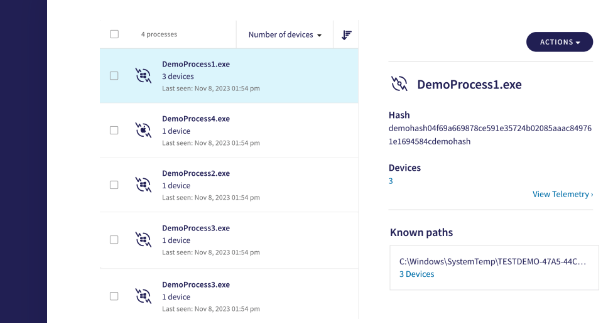
The Endpoint Detection and Response (EDR) module extends your ability to handle incidents as they occur. You can remediate quickly to prevent further damage from known and unknown threat sources and to conduct post-breach analysis. It continuously monitors endpoint devices and presents these findings in clear, easy-to-manage tabs from the Coro dashboard. Filter through the data as needed, and receive remediation guidance and immediate response actions.
Capabilities:
- Enhanced malicious software detection.
- Proactive isolation of infected devices.
- Automatic remediation across endpoints.
Endpoint Data Governance
The Endpoint Data Governance module protects sensitive data from unauthorized access, use, disclosure, modification, or destruction across endpoints. To help ensure compliance with these regulatory standards, Coro lets you remotely scan endpoints for:
- NPI (non-public information).
- PCI (payment card information).
- PHI (protected health information).
- PII (personally identifiable information).
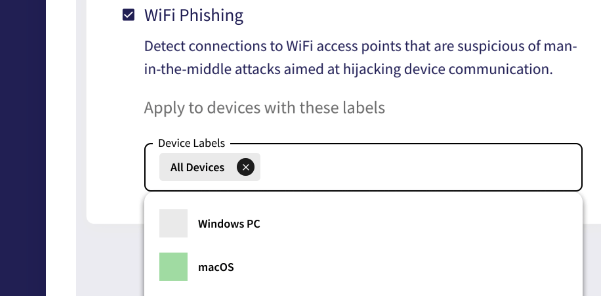
Wifi Phishing
The WiFi Phishing add-on guards endpoints outside the LAN (local area network) by preventing connections to suspicious WiFi access points. It works by detecting connections to WiFi access points that are suspicious of man-in-the-middle attacks aimed at hijacking device communication.
Protects:
- All devices in your workspace.
- Specific groups of devices.
- Remote/ traveling employees.
Mobile Device Management
Mobile Device Management (MDM) enables you to manage iOS and Android mobile devices used by end users across your organization.
Capabilities:
- Report on mobile device activity and usage.
- Remotely wipe data from compromised devices.
- Enforce app policies across your company-owned devices.
Additional Information
Terms & Conditions
Terms of Service
https://www.coro.net/termsPrivacy Policy
https://www.coro.net/privacyResources
Coro Endpoint Data Governance Module - Datasheet
Powered by WHMCompleteSolution