End-to-end protection against identity threats
$73.33/year
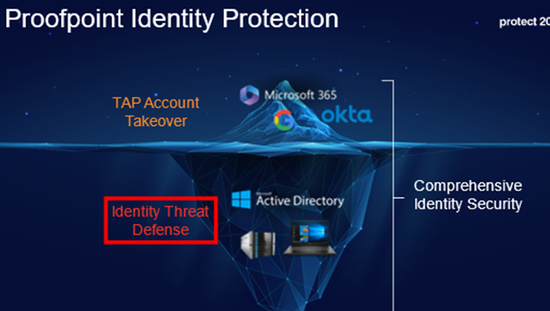
Proofpoint Identity Threat Defense provides comprehensive protection against identity-based cyber threats, such as account compromise, credential phishing, and identity fraud. It uses advanced behavioral analytics and AI to detect, mitigate, and respond to threats targeting user identities. The solution integrates seamlessly with enterprise systems, providing real-time threat intelligence and automated remediation. By safeguarding identities, it reduces the risk of unauthorized access and enhances overall security posture, ensuring compliance and protecting sensitive data.
Top Features
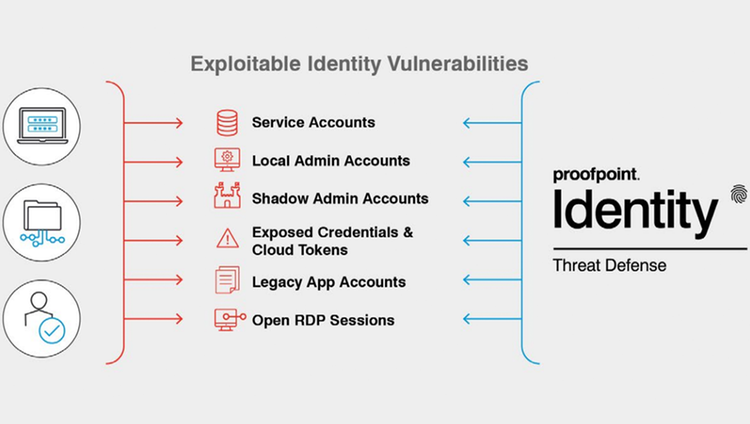
Gain visibility into identity vulnerabilities covering Active Directory, Entra ID, AWS Identity Center, Okta, PAMs, Endpoints, LAPS
Understand the privileged identity risks and available attack paths in your environment
Discover, prioritize and remediate identity-based vulnerabilities
Automatically remediate identity vulnerabilities exposed on endpoints
Ensure early attacker detection and accelerate threat investigations
Use agentless technology that attackers cannot bypass
Fill the gaps left by signature- and behavior-based threat detection
Leverage integration with Proofpoint TAP, TAP ATO and NPRE
Available for SaaS deployment
Recommended products
An end-to-end view of Identity security
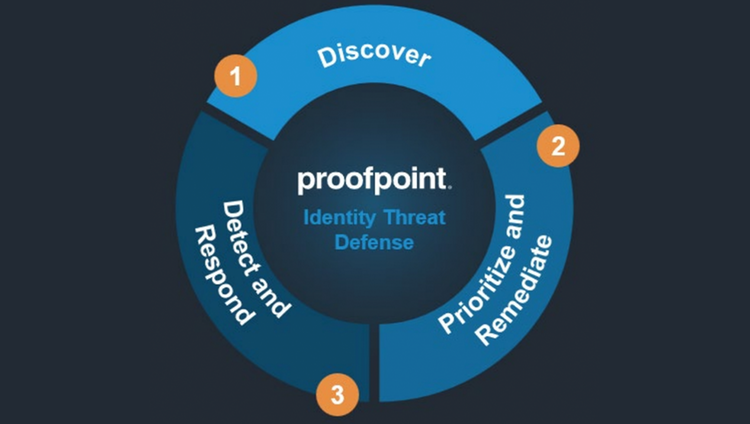
Successful attacks exploit management and protection gaps. Our platform helps security leaders see and defend against these gaps. It enables them to:
Discover
Get continuous discovery and visibility of identity vulnerabilities in AD, Entra ID, AWS Identity Center, Okta and endpoints.
Prioritize and remediate
See a list of vulnerabilities prioritized by the ones that need attention first. These risks appear on a spectrum that ranges from non-critical to urgent. Enable automated remediation of identity vulnerabilities straight from the platform. You can set up exception rules that are consistent with your security policies.
Detect and respond
See when attackers are active in your environment. With agentless deceptions, you can detect activity such as kerberoasting, password spraying, privileged account abuse and much more. You can use automated forensic data collection to help guide your organization’s response to active threats.
Additional Information
Terms & Conditions
Terms of Service
https://www.proofpoint.com/us/legal/licensePrivacy Policy
https://www.proofpoint.com/us/legal/privacy-policyResources
Proofpoint Identity Threat Defense - Solution Brief
PFPT Identity Threat Defense Platform Bundle (Spotlight + Shadow) - Channel Only
$10.40User/yearPFPT Identity Threat Defense Platform Bundle (Spotlight + Shadow) - Channel Only
$10.40User/yearPowered by WHMCompleteSolution