Unified security solution for users, devices and access
$4.30/month
Check Point Harmony Mobile is the market-leading Mobile Threat Defense solution. It keeps your corporate data safe by securing employees’ mobile devices across all attack vectors: apps, files, network and OS. Designed to reduce admins’ overhead and increase user adoption, it perfectly fits into your existing mobile environment, deploys and scales quickly, and protects devices without impacting user experience nor privacy. Harmony Mobile addresses all those concerns providing advanced protection from all kinds of mobile threats and across all attack vectors (apps, network and OS). By using the innovative zero-touch deployment, organizations can swiftly extend their secured devices from zero to tens of thousands.
Top Features
Prevents malicious app downloads
Prevents phishing and zero-day phishing from all apps
Prevents man-in-the-middle attacks
Blocks infected devices from accessing corporate assets and resources
Detects advanced jailbreaking and rooting techniques
Detects OS vulnerabilities (CVE) and misinformations
Recommended products
User friendly
Quick user adoption with zero impact on user experience or privacy.
Privacy by design
User and corporate data kept completely private; no personal information is collected or analyzed at any point. Harmony Mobile never analyzes files, browser histories, or application data. The solution uses state and context metadata from operating systems, apps, and networks to determine if a device is compromised. It anonymizes the data it uses for analysis in order to keep it protected.
Elegant user experience
No impact on device usability and browsing experience; the on-device app performs without draining battery life or data consumption.
User education
Employees become increasingly aware of mobile security risks with detailed threat real-time notifications and weekly summaries.
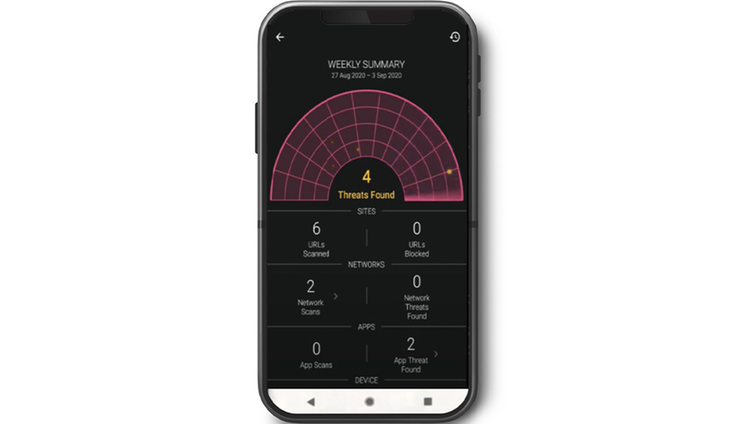
Simple management
Scalable and easy-to-manage security for any type of mobile workforce.
Zero-touch deployment
The on-device app installs on employees’ devices with a single click and without their interaction, leveraging your existing MDM/UEM.
Tailored protection for all android enterprise deployment models
Harmony Mobile protects both work and personal profiles to ensure comprehensive threat prevention.
Easy to manage
A cloud-based and intuitive management console provides the ability to oversee mobile risk posture and set granular policies. Harmony Mobile also expands your mobile application deployment security by giving administrators an application vetting service, allowing them to upload or link applications (both Android or iOS) into the Harmony Mobile Dashboard and receive a full app analysis report within a few minutes.
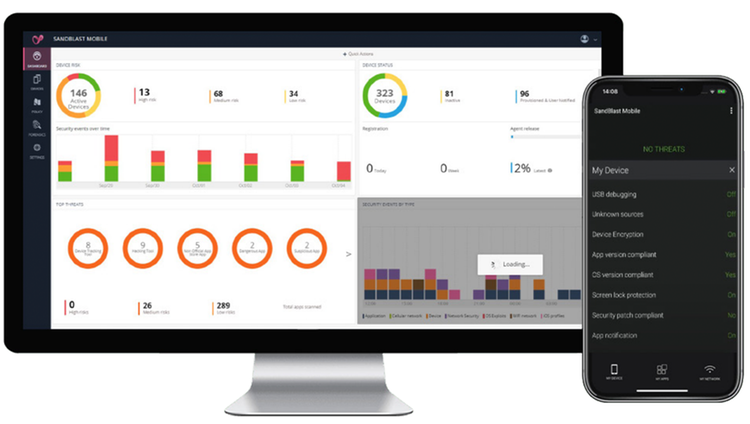
Complete protection
Protecting corporate data across all mobile attack surfaces.
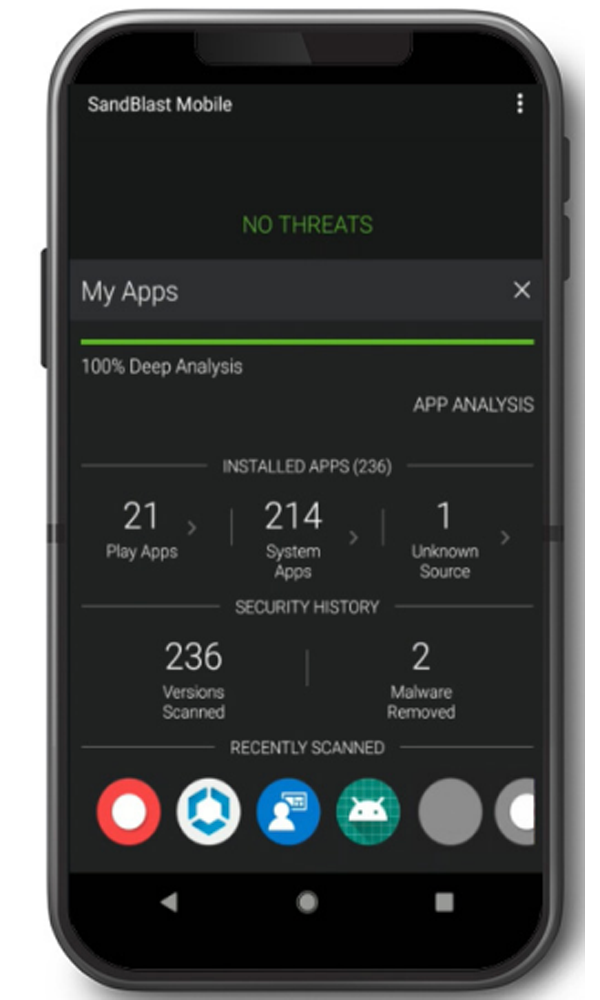
App & file protection
- Check Point’s unique Behavioral Risk Engine runs applications in a cloud-based environment to determine if an app is malicious, leveraging machine learning and AI, sandboxing, advanced static code flow analysis, anomaly detection, and app reputation among other techniques. Mobile application scanning is available offline as well.
- By processing the signatures of the downloaded files and accessing them using the Check Point ThreatCloud™, Harmony Mobile can detect and block malicious files even before they reach the users’ device storage, by then, preventing any damage to the corporate assets. Harmony Mobile also enables scanning the end users’ device storage so infected files are kept out of the organization boundaries. Zero-day file-based attacks are be blocked by real time cloud-based sandboxing.
Network protection
- Anti-phishing with zero-phishing: Blocks phishing attacks across all apps, both from known and unknown zero-day phishing sites.
- Safe browsing: Blocks access to malicious sites from any web browser, leveraging the dynamic security intelligence provided by Check Point ThreatCloud™.
- Conditional access: Blocks infected devices from accessing corporate applications and data, independent of UEM solutions.
- Anti-bot: Detects bot-infected devices and automatically blocks communication to command and control servers.
- URL filtering: Mark websites as “blocked” or “allowed”, preventing access on any browser to websites deemed inappropriate by an organization’s corporate policies.
- Protected DNS: Allows administrator to manage and control all mobile device’s DNS preferences. The service protects end-users privacy and prevents MiTM attacks & DNS Spoofing of plain text DNS messages.
- Wi-Fi network security: Detects malicious network behavior and Man-in-the-Middle attacks, and automatically disables connections to malicious networks.
OS and device protection
Ensures devices are not exposed to compromise with real-time risk assessments detecting attacks, vulnerabilitie (CVE) management, configuration changes or weak security settings, and advanced rooting and jailbreaking. Harmony Mobile provides a full, synthetic and actionable vulnerability assessment by running an extensive inventory of known vulnerabilities in the installed mobile operating system. Based on this data, security admin can easily identify risky devices, block their access to the corporate resources and prevent OS exploits.
Additional Information
Resources
Check Point Harmony Mobile - Demo
In this video, we explain how to run a demo on Check Point Harmony Mobile from the test device on-boarding process, via posture management to the unique network protection capabilities.











