Preventing breaches with cloud analytics, AI & real-time visibility
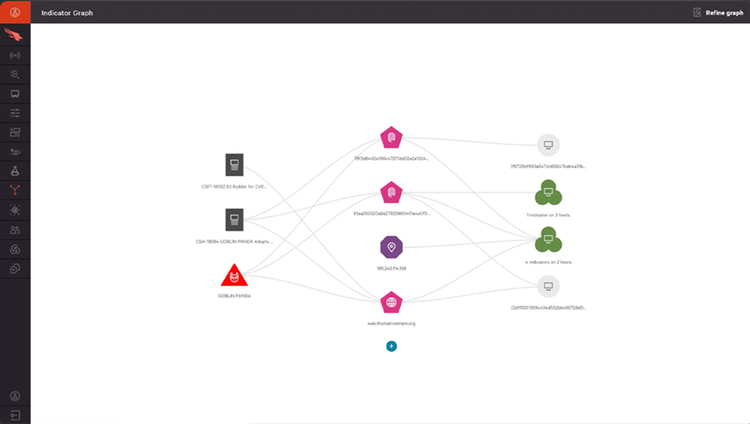
CrowdStrike Falcon Threat Graph is a powerful cloud-scale AI engine that is the backbone of CrowdStrike Security Cloud. We leverage advanced AI capabilities to predict and prevent modern threats in real-time. We offer several advantages, including comprehensive data sets, cloud-scale analytics, real-time attack visibility, and maximum security efficiency. We are equipped with purpose-built graph databases for cybersecurity, enabling fast investigation and response through contextual relationship derivation with ML algorithms. We provide real-time visibility with enriched data and intuitive dashboards, covering various types of hosts to empower responders with immediate and decisive actions against threats.
Top Features
Comprehensive data sets
Continuous high-fidelity telemetry with forensic-level detail across endpoints and workloads distributed across the network edge and hybrid cloud infrastructure — including Windows, macOS, and Linux, together with cloud-native storage for always-on data availability.
Real-time attack visibility
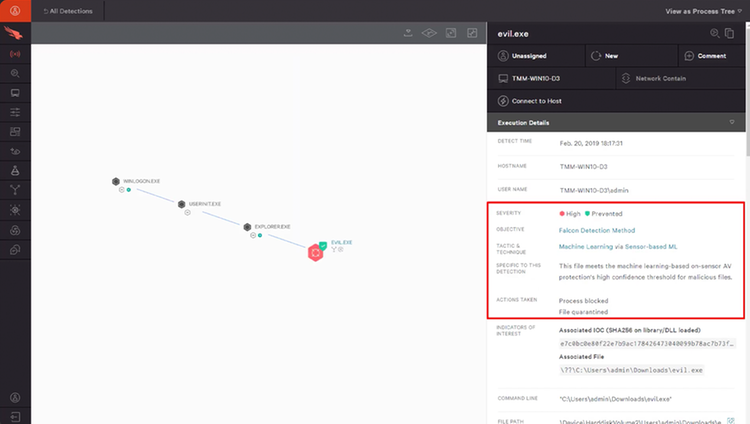
Real-time visibility with instant access to enriched data and intuitive dashboards for advanced workflows and visualizations — covers ephemeral, online, offline and even end-of-life hosts to arm your responders with data so they can respond to threads immediately and act decisively.
Cloud-scale analytics
Contextual relationship derivation with ML algorithms and deep analytics across billions of disjoint and siloed data elements — allows for fast, on-demand search and query across real-time and historical data for speedy investigation and response.
Recommended products
Power of security cloud
Harness the security cloud's formidable strength for comprehensive protection.
Fully operational in minutes
Complete turnkey solution with no additional hardware or deployments.
Power of the crowd
Use network effect to protect everyone against a new threat, regardless of where it is encountered.
Zero maintenance overhead
See value from Day One, with no additional custom tuning, costly consulting, re-architecting or maintenance overhead.
Scale and elasticity
Automatically scales and grows with demand and change.

Power of data
Unlock the transformative potential of data to drive innovation and informed decision-making.
Enriched telemetry
Capture trillions of security events across endpoints, workloads and identities and enrich with threat intelligence, context and correlation markers.
Deep analytics
Reveal contextual relationships between data elements to identify and respond to new and unusual threats in real time by applying graph analytics and ML algorithms.
Powerful search
The robust query and search engine provides current and historical forensic details to arm responders for threat investigations.
Data availability
On-demand access to enriched data with powerful visualization dashboards helps investigators understand the full context of the attack on any affected host, regardless of location.

Maximum security efficiency
Optimize security operations for maximum efficiency and effectiveness.
Actionable insights
The industry’s leading collection of powerful insights gathers more than a trillion events per day spanning across 2 trillion vertices and analyzing over 15 petabytes of data.
Integrated threat intelligence
Telemetry is enriched with real-world threats and identifies new attacks associated with known threat actors.
Accelerated response
Real-time visualization and automated concurrent analysis lead to faster investigation and response times.
Proactive threat hunting
Threat hunters can run ad hoc queries for successful and timely detections of unknown threats.

Single source of truth
Establish a single, authoritative source of truth for accurate and reliable information.
Single data source
Gain rapid access to everything required to prevent, detect, investigate, and respond.
Single intelligent agent
The lightweight agent provides smart-filtering capability streams relevant data for enrichment and correlation to the Threat Graph — with no performance impact.
Robust set of APIs
Powerful APIs allow for security orchestration, automation, response and other advanced workflows.
Rich integrations
APIs and bidirectional data flow enable tight integrations with third-party security and IT solutions to share insights from multiple data sources.
Cloud-delivered resources
Threat Graph scales with demand and provides necessary storage, computing and rich analytics required, with up to a year of all detections encountered.
Enriched data archive
Optional offline replica of enriched telemetry is available for archive, compliance requirements and additional analytics.
Additional Information
Terms & Conditions
Terms of Service
https://www.crowdstrike.com/website-terms-of-use/Privacy Policy
https://www.crowdstrike.com/privacy-notice/