Harden cloud security and reduce the risk of a breach
$49,500.00 /Month
Spot Security provides the key capabilities to deliver a robust cloud security program for an organization. With Spot Security, you can ensure secure configurations, remove vulnerabilities & threats, maintain compliance, manage access rights & protect your business-critical assets — all with one integrated solution for your cloud infrastructure. Spot Security is an agentless solution that gives you holistic visibility of your security posture in real time. Since not every issue can be addressed on day one, Spot Security provides an accurate, relevant list of misconfigurations, vulnerabilities & threats prioritized based on their urgency & criticality to your business, together with guided & automated remediation so you can fix them first.
Top Features
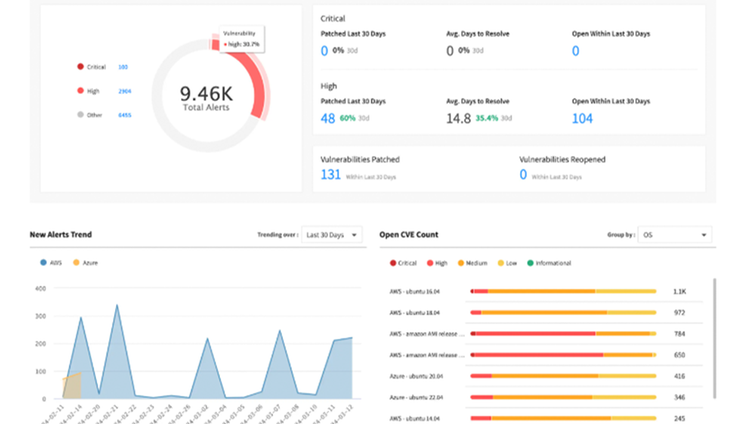
360-degree visibility
Get a unique perspective of your entire cloud security posture. Identify, map, correlate and contextualize risk attributes, including misconfigurations, vulnerabilities and threats, access permissions, and compliance.
Surface & prioritize
Find the risks that matter most. Get an accurate, relevant list of vulnerabilities, misconfigurations and threats, prioritized by their urgency and criticality to your business.
Remediate & secure
Reduce risk fast. Get proactive notifications, guided/automated remediation and incident response workflows and enforce least privilege access.
Recommended products
Fix the highest priority risks to your business in the least amount of time
Designed for the cloud, Spot Security is an agentless solution that gives you holistic visibility of your security posture in real time. Since not every issue can be addressed on day one, Spot Security provides an accurate, relevant list of misconfigurations, vulnerabilities and threats prioritized based on their urgency and criticality to your business, together with guided and automated remediation so you can fix them first.
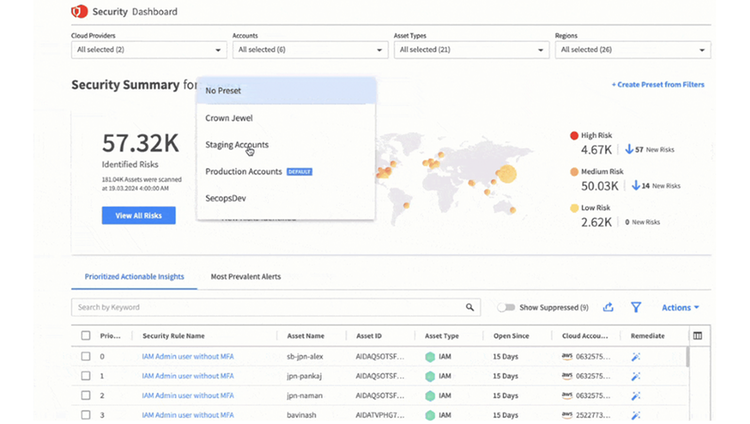
Gain a single view of your security
Get a prioritized 360-degree view of risk based on the severity, attack surface and network exposure – all in one dashboard.
Focus on the real risk to critical assets
Easily uncover even seemingly minor gaps in your security posture that put critical assets and IP at risk.
Understand the risk impact
Correlate and contextualize risk attributes to prioritize the risks that have the greatest impact on your business.
Remediate quickly and easily
Save time and effort with proactive alerting, guided or automated remediation and incident response workflows.
How Spot Security can help you
With Spot Security, you can ensure secure configurations, remove vulnerabilities and threats, maintain compliance, manage access rights and protect your business-critical assets — all with one integrated solution for your cloud infrastructure.
Safeguard business-critical assets
Track the security posture and compliance status of business-critical cloud assets and services.
See the potential impact of misconfigurations, threats and vulnerabilities.
Easily create remediation workflows.
Detect and remove misconfigurations
Get a complete picture of all misconfigurations.
Immediately identify the most critical misconfigurations, prioritized by severity.
See the blast radius of each risk to understand the impact on assets.
Find and remediate vulnerabilities
Uncover vulnerabilities in VMs using the NVD and MITRE ATT&CK framework.
Get deep insights, and understand the impact across the cloud to focus and streamline remediation.
Uncover anomalies and threats in real time
Significantly reduce false positives with machine learning (ML)-based threat detection.
Easily create incident response workflows for your security teams.
Detect threats in real time using the MITRE ATT&CK framework.
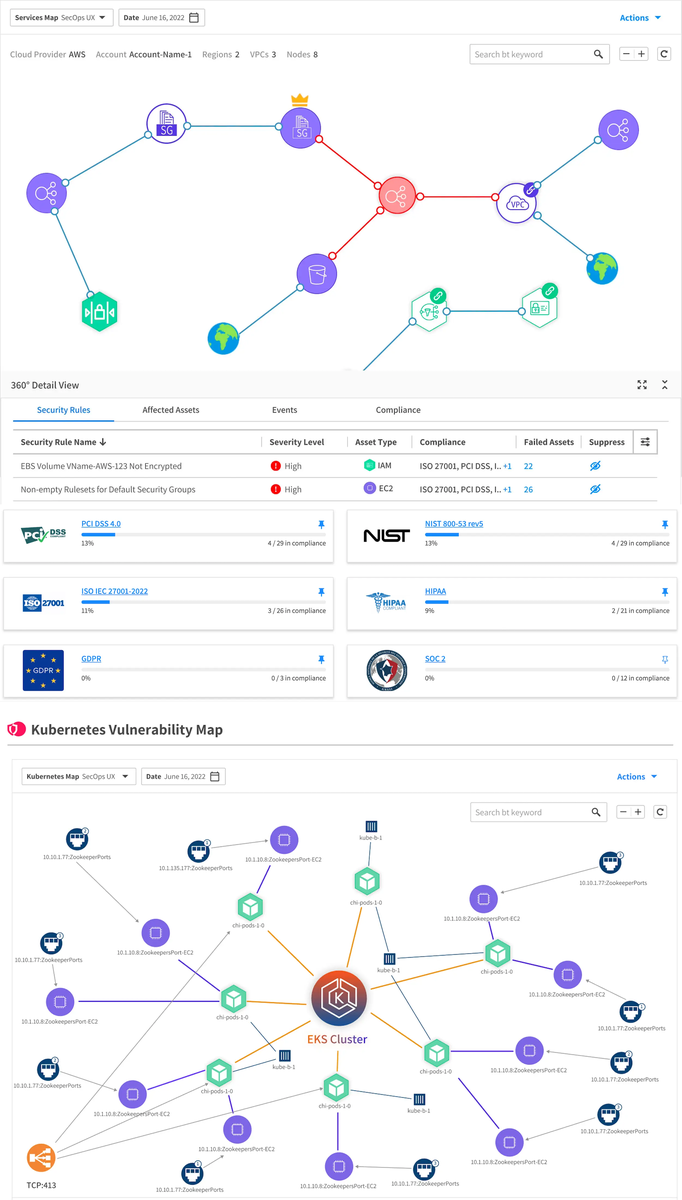
Protect Kubernetes workloads
Know if your Kubernetes services are configured correctly.
Immediately detect misconfigurations and compliance drifts.
Track compliance and support auditing
Automatically track compliance of your cloud against key industry regulations.
Provide evidence for audits.
Generate reports for enterprise, specific regions, business unit or any other parameter.
Enforce least-privilege access
Know who is accessing your business-critical cloud assets and services.
Eliminate overly permissive or duplicate access rights.
Implement ready-to-use policies to enforce least-privilege access.
Proactively prevent security flaws in infrastructure code
Detect potential vulnerabilities and misconfigurations as you write your code.
Get recommendations to write secure code.
Prevent risky code from being deployed.
Additional Information
Terms & Conditions
Terms of Service
https://www.netapp.com/how-to-buy/sales-terms-and-conditions/Privacy Policy
https://spot.io/security-policy/Resources
Spot Security - Manage your Cloud Security Posture
Watch the video to learn more.